FUD FIVE : Misinformation and Disinformation Warfare
This post is a cross post from my LinkedIn page, incase anything happens.
Ok that was as close as I could get ‘Fast Five’ the 5th Fast and Furious Movie as a title…
It is 6:51am.
I shared an post by Gregory Bufithis 🇺🇦 last night to my following on LinkedIn:
I discovered this post after I was tagged in the comments section, those comments have now been removed as they do not follow the authors clearly bias point of view on the subject matter.
The Subject Matter?
Andy Jenkinson being referred to as an expert, in particular this last paragraph:
As my regular watchers and blog readers know, Andy is a well-known and oft cited expert in cybersecurity and the complexity of our cyber infrastructures, and the mind-boggling demands of internet security. This interview will be a revelation to many.
That alone terrifies me.
To think you can have an ‘oft cited expert’ who still doesn’t know the difference between an SSL cert and a DNS record, or that the Ad Block extension he has installed on the same browser he logs into his Microsoft Outlook email, is actually Malware…
It has been previously noted that Andy is under the impression that an expired or Missing SSL cert means that the site owner is open to a compromise and that Microsoft DNS servers (read: RESOLVERS!!!) are the culprit.
They are not.
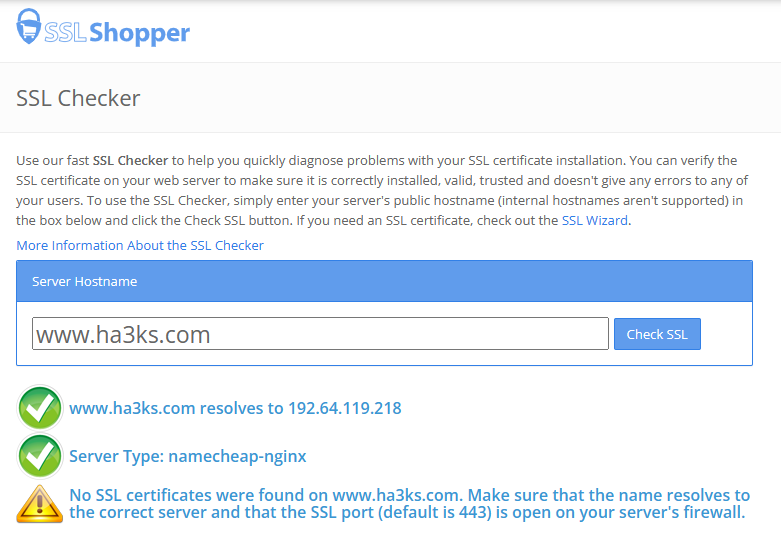
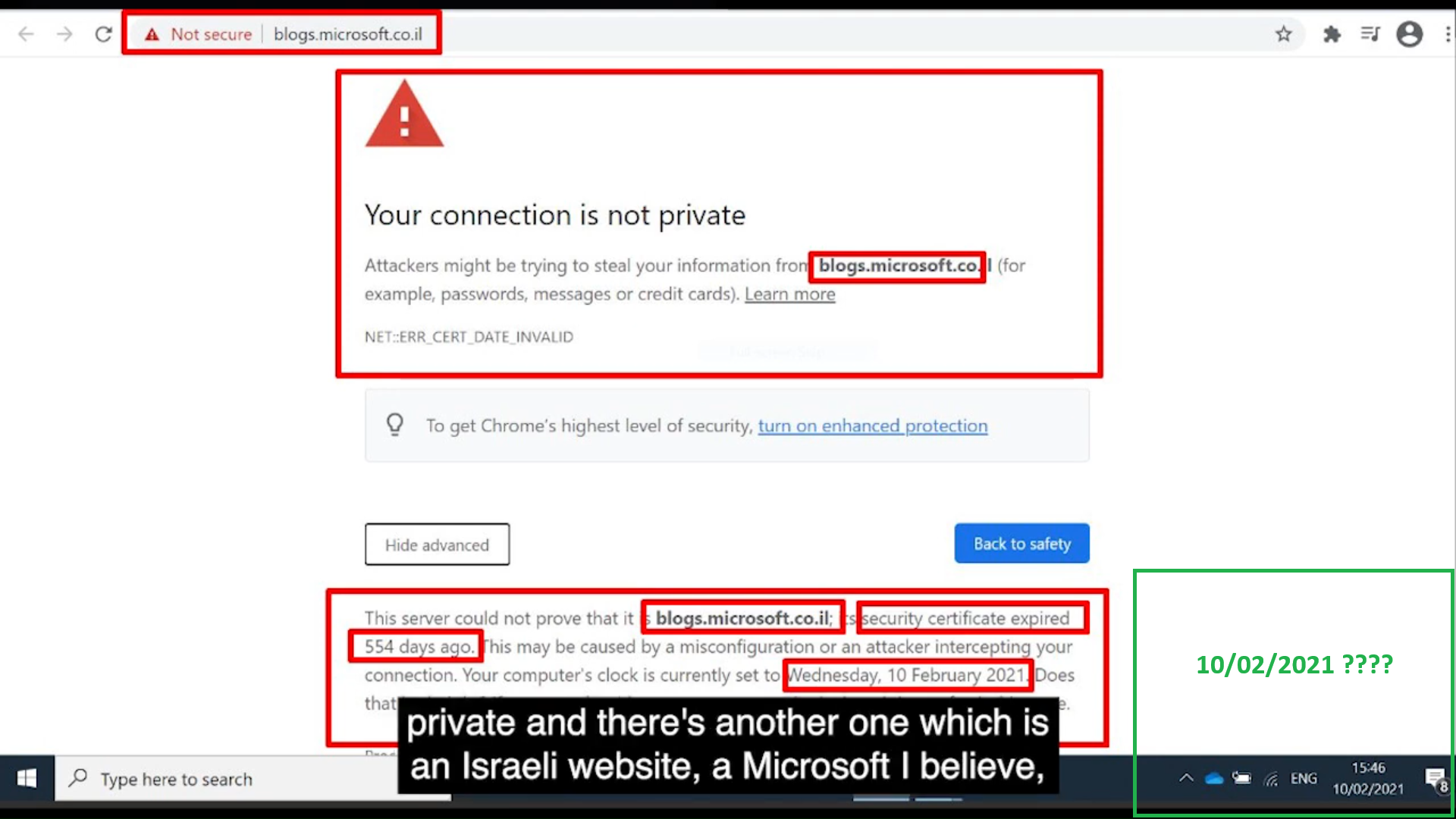
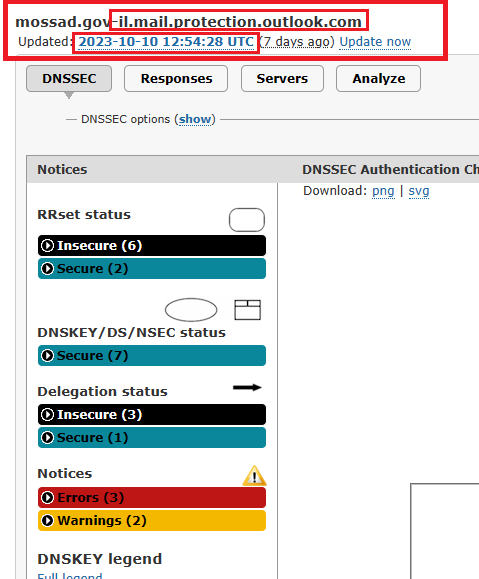
Infact I disproved this previously in the comments section of another post because my site, ha3ks.com DOES NOT have an SSL cert:
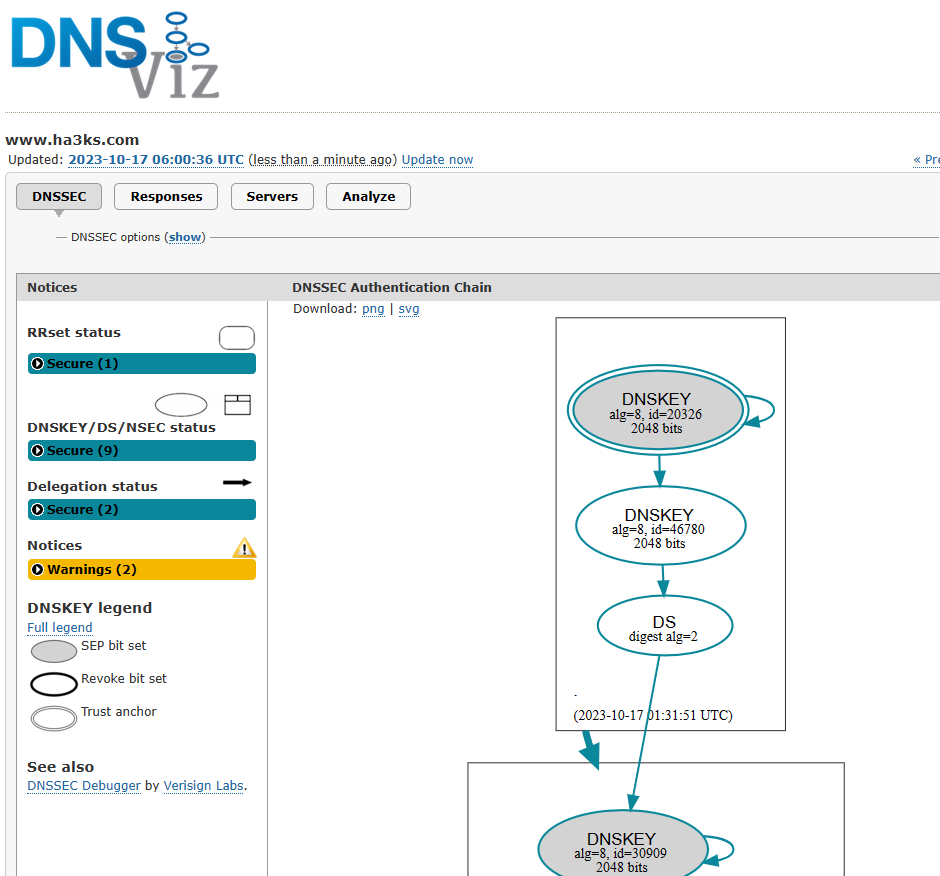
But…. The DNSSEC of ha3ks.com is tighter than an Italian waiters keggs (underpants for those who don’t know the phrase or didn’t watch Red Dwarf):
Hey would ya look at that, 2 of Andy’s favorite sites to check things and put in red redaction boxes… almost as if they are completely free resources anyone can use… shocked Pikachu face
So what does this mean?
Well to be candid, as Andy likes to be when he is backed into a corner on a post, Andy’s technical understanding as an expert appears to be; ‘Keywords and hope they mix together somehow’.
Why is this a bad thing?
Well, do you remember that time when the BBC were doing an interview of Guy Goma live on air believing him to by Guy Kewney, the editor of NewsWireless?
I think about that interview a lot, about how someone could make such a miniscule mistake and it leads to a cleaner being interviewed live on TV…. I think of Andy Jenkinson in that situation.
The problem with that is Andy is now what I would classify as ‘Dangerous’ he knows just the right amount of theory and verbiage to con his way into peoples wallets and convince others who have a feint interest in something that he is the defacto expert and his word is backed up by god.
The Interview Itself
Now this is a tricky one.
I am going to be upfront about this; I am not an expert in ‘Cyber Warfare’, I am not an expert in ‘Actual Warfare’. There is absolute atrocity and war crime happening right now on this very tiny little blue and green marble we call a planet, a home, all as it falls slowly through the universe.
I am not commenting on this war and I am not qualified to, the fact Andy would and so openly is once more why I now believe him to be dangerous.
Now I do know people who are in that field of Cyber Warfare and actual ‘Violence of Action’ Warfare… I believe them to be experts as they are ‘boots on the ground’ to borrow some military vernacular.
It is very clear that Andy is taking part in what’s called ‘Ambulance Chasing’ which is very poor taste and very clearly shows how low he is willing to go to remain relevant and something on peoples minds, vanity or something…
What I do know however, is Cybersecurity:
Specifically I have multiple certifications in this field and enjoy spending my time learning about new tools and techniques as well as torturing my SSDs with constant rebuild and lab construction and destruction.
I am practiced.
I am sharp.
I am getting sharper.
As such I have watched (yawned) my way through this one hour and six minute interview and picked up on the parts that only relate to the field of cybersecurity. As far as I am concerned everything else is is ‘take a mountain of salt’ territory.
So here we go, point and counterpoint style:
00:00:52 - 00:01:03
A series of interviews with people that I think are expertise in certain areas. And Andy, who I’m gonna get to in a minute, is certainly one of them.
A series of interviews with people that I think are expertise in certain areas. And Andy, who I’m gonna get to in a minute, is certainly one of them.
In my opinion you should be impartial and let the listener connect the dots and believe what they choose to believe, not someone else’s narrative.
00:01:12 - 00:01:24
And it’s interesting because Andy is one of those guys who’s really a pain to interview with because he backs up everything he’s saying with exhibits, information, et cetera.
Ok so he admits Andy is a pain to interview, I would agree (hahahahahaha free laugh) but only because he backs up everything he is saying.
Well this is a bit of a double edged sword because an ‘expert’ would backup everything they are saying with evidence BUT Andy’s evidence is proven time and time again to be fabricated and lies… half points on this one?
00:03:33 - 00:03:43
If you follow him on LinkedIn, you realize that he very often knows way ahead of mainstream media, most of us, what’s going on and what’s going on behind the headlines.
True, he does apparently know what is going on way ahead of people… If you look closely i.e. scroll maybe a few of his posts you will see patterns in them, patterns as to what tools are being ‘misused’ and why it is every single time a new threat appears the screenshots come out specific to that threat and the stories of ‘I’ve been emailing them for month’s with no answer’ when in actuality Andy showed his hand on that one as he screenshotted his LinkedIn DMs to those persons,,, LinkedIn DMs are not a paper trail of email specifically to that person.
Suddenly the ‘True, he does apparently know’ becomes ‘True, he does make up a lot of stories to fit a narrative of screenshots he just made earlier that day,’
00:03:59 - 00:04:22
the cusp of understanding the solar winds cyber breach that was executed by the Russians back in 2020 in fact if you pardon me if I’m reading um it was Andy’s research paper and his analysis that was presented to the United States intelligence United States Senate intelligence committee uh back in January 2021 when they were giving this examination
Where to start with this one, We (that is cybersecurity professionals) know that SolarWinds was a Supply Chain Attack, code was added to the Orion system which is a part of the lets say ‘back end’ of SolarWinds software.
This isn’t DNS so I’m not entirely sure why Andy’s research would be even looked at by the Intelligence Committee.
00:04:47 - 00:04:50
He even appeared in an interview with the Vatican news agency.
I skipped over this part initially then found out it was actually him emailing about subdomains and was published only in the Catholic News Agency online - Cyber security expert urges Vatican to strengthen internet defenses against hackers - Catholic News Agency
I mean, trying to flog your wares to ‘God’s appointed and holy representative on the Planet Earth’…….
I can’t say the expletives I want to for this but know they are many, and varied.
00:07:35 - 00:08:55
in reality we discovered that the notams servers had actually been um what we call command and control was no longer explain those servers those servers basically they allow uh the notime servers allow all information sharing to and from the FAA to every single pilot okay that’s flying across the US airspace and and the same is for every country across the world those servers tell you if it’s safe if you need to land or if there’s a like the Icelandic you know volcano ash cloud it tells these guys what they can and can’t do and what had happened is the digital certificate we can go into as much information as you want it’s like a digital passport that had been allowed to um lapse the servers were not secure and the only way the FAA could actually be assured of not um potentially allowing a digital 911 was to shut down the airspace, we helped them and obviously as I say I was up at 6:30 that morning and and going through the stuff that we do and by 11:30 uh they’d come online and they were actioning the information we provided to them.
A bit to unpack here, Andy sure does like to use more common wording to make it seem like the thing he is talking about is relatable, Digital Certificate = Passport, Command and Control, Digital 911. Often this wording is used to shock people into submission.
The Notams servers though, this is because of an expired SSL cert, nothing more, nothing less..
Somehow Andy had a login for the NATS service in the UK - NATS UK - Home (ead-it.com) and decided to plaster DNSViz screenshots of something similar to “nats-uk.mail.protection.outlook.com” which would give an error as proven time and time again, my previous article(s) expand on this:
Leading people who are not knowledgeable on DNSSEC or what any of the warnings are errors are (and what’s hidden behind his red redaction lines) to believe it’s an actual problem or threat and Andy discovered it first because of screenshots.
It’s really not, check out that article ‘smoke and mirrors’ it explains what happens when you use a tool improperly and why it’s always ‘those’ screenshots.
I can assure you dear reader that the servers are quite secure and operating in an entirely different space to what Andy claims he has access to.
00:11:04 - 00:11:35
websites servers and domain name systems when not secure is like leaving shop fronts wide open that enables very easy passage for cyber criminals to gain access and the bit that many people don’t understand is that a website typically a company will have hundreds if not thousands, a website can give you access to email our systems the network and the infrastructure all the way up to as we say command and control which is what happened at solar winds in 2020
Big oof Andy, SolarWinds wasn’t a ‘digital shop that criminals accessed’, SolarWinds was, say it with me now ‘A Supply Chain Attack’. I’ve pointed that out earlier in this article too and many websites like BusinessInsider have articles on it too.
Again though, using language that many people would understand is fantastic for education BUT the way Andy is specifically using it is to ‘dumb down’ actual issues.
Again just because the shop front is wide open doesn’t mean it is insecure cough ha3ks.com cough A shop in the literal sense can have internal security cameras, undercover security guards, tagged items and barriers, the list is endless so you cannot attribute an open door a massive gaping hole in security its just ‘a little’ more complex than that.
00:11:55 - 00:12:17
Screenshots, our favorite talking point from Andy, always redacted, always broken. Often the screenshots are for pages that no longer exist or are no longer valid/abandoned.
Wait, what the f**k look at the green addition I made to Andy’s original screenshot, check out the date, 2021? how is that even relevant anymore?:
And the other mentioned redirects to the actual site which is secure:
How can we be sure that Andy hasn’t just rolled back the date on his computer again to F with the Certs showing them all invalid?
Ima calling Bullshit on that one.
00:12:14 - 00:14:37
I’ve decided I’m not going to quote as many now (hopefully), trying to enter the transcript of the conversation takes up too much time.
Andy is explaining what an SSL cert is and that having one missing is a potential that there is a problem with the cert or problem with the site, makes sense right? He seems to believe that not having one should be a massive warning to visitors of sites that ‘if you use this site cyber criminals will get your details’
No they wont. The SSL cert refers to if your site can accept secure sockets of connection as opposed to, I guess we could call it ‘open transmission’ where other people if they possess the knowhow could view or tamper your request.
If you are playing Andy Jenkinson Drinking Bingo Game at home he said ‘Exploitable Positions’, not exposed positions so hold hack on that shot just for now.
00:14:50
He says 30,000 websites a day are hacked, doesn’t elaborate on what that is, could be defacement, could be accessing the back end database, could be just a simple crash. Numbers without facts to back them up are meaningless.
00:15:34
Relates the FAA hack to hackers 7000 miles away when someone could have easily plugged in a USB Rubber Ducky and got remote access, so he’s trying to blame ‘exposed internet connectivity’ as the source.
00:15:59
Gregory : I don’t have I’m assuming I don’t have the well with all or the or the technology
Andy: um not quite true I could teach you in in a reasonable time
Oh god, can you imagine Andy teaching someone to test against unsuspecting and unknowing targets? First rule of conducting research, have permission from the person/company you are testing against. The Second Rule of conducting research is, YOU HAVE TO HAVE PERMISSION FROM THE PERSON/COMPANY YOU ARE TESTING AGAINST!
Andy absolutely hasn’t done that and that can be evidenced by his attempt to fleece CrowdStrike and then con his audience into believing that he contacted CrowdStirke and they acted on his warning. THEY ABSOLUTELY DID NOT!
A post I made on this lie:
00:16:15
what we do is we will show the vulnerabilities and exposure that’s where it stops
So Cybersec Innovation Partners will find an expose your vulnerabilities, write a report with possibly no red redactions in it (though likely they are still in there) and that’s it?
No advice on remediation?
No coming back to retest in a few months when actions and recommendations should be in progress/complete?
00:17:17 - 00:17:20
‘Exposed Positions’
DRINK!
00:18:40 - 00:19:00
Microsoft have 8.5k staff on security. - Maybe, I mean I don’t know for sure as they are ABSOLUTELY ENORMOUS(!!!) and that recent acquisition of Blizzard at $69 BILLION also added a few more staff to the roster, but Andy is implying that they have all these staff and they can’t fix or specifically won’t fix all these ‘exposed’ DNS servers.
Ignore the fact that they don’t actually belong to Microsoft so it isn’t their issue. But take into account that the only reason he has such a hard of for Microsoft is that he uses “.mail.protection.outlook.com” which is always broken and always will be broken as evidence in his screenshots.
A Video I did on this:
00:19:30
Andy goes back to his first screenshot and specifically points out that the ‘Security Certificate Expired 544 days ago so in other words that website had been insecure for at least a year and a half before we found it’
Yes/No it doesn’t.
It means that the site may not have worked with secure socket connections for 544 days prior but the absence of the certificate itself doesn’t mean the site was insecure (remember the shop front analogy from above, there could be other things in there acting as security).
00:20:38
Oh look, another screenshot… let’s get the whole picture though not just your shoddy edit:
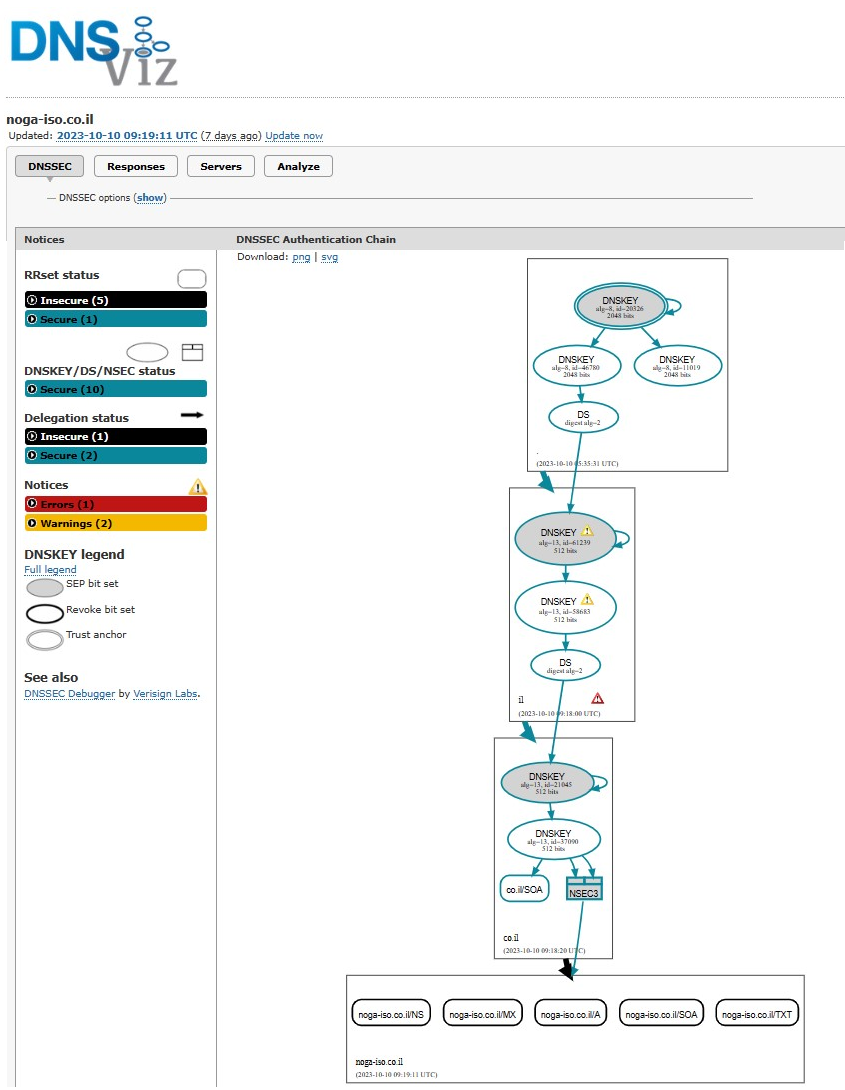
The bottom segment of the DNSViz site which shows the ‘end’ DNSSEC of a domain shows Insecure.. let’s have a closer look:
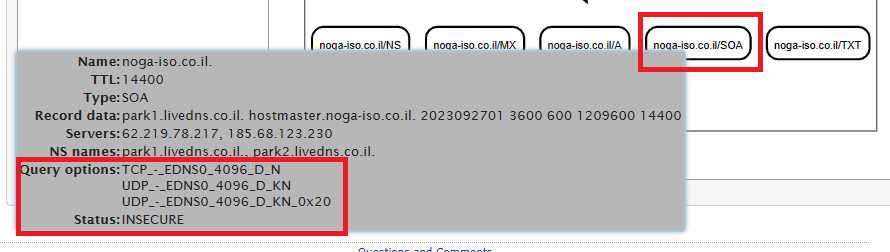
Ah ok so the reason it shows as ‘insecure’ is because the server that is hosting the record (not the site itself) is not responding to the DNSViz testing queries via TCP or UDP.
So in other words….. It’s still secure, and DNSViz won’t show the full progression of the test because it can’t get past that stage which is CORRECT in this instance.
100 points to Gryffindor! I mean DNSViz for doing exactly what it should be doing in these instances.
00:20:55
Aww Andy thinks that Dr. Paul Mockapetris (The Inventor of DNS) has become a reasonable friend of his, I wonder if Paul knows that Andy doesn’t quite understand DNS and he uses it to flog an expensive report? I wonder why Andy never mentioned in any article or post previously Paul by name till I pointed it out in a FUD Fighters Article.
Coincidence?
00:21:25
Uses the Old Skool example of what DNS is, a phonebook for websites. This might be the only actual thing Andy knows that is correct about DNS at this point.
00:21:58
Makes reference to Edward Snowden, the whistleblower on surveillance, that he exposed surveillance on DNS facepalm
Cyber Crime didn’t go up because of the ‘revelations’, it may have been more ‘noticeable’ but the popularity of the internet has gone up as time has gone on, so obviously the crime would go up too… it’s impossible to state that these two things are connected, infact it’s outright stupid to assume that.
00:23:40
Screenshot of the Contact Page for the National Security and Defense Council of Ukraine.
I said I wasn’t going into ‘war’ stuff and I am not but I have to point out, this is a contact page, it has no functionality other then giving a phone number and an address.
Andy is using what looks to be Google Chrome, the date given is plastered in the center of the screen that he has written instead of the actual computer clock so that’s absolutely meaningless as it could be yesterday for all intensive purposes and he is using AdBlockPlus a fairly well known Ad Blocking extension, but not many people realize it does infact serve ads and does… lets say ‘other’ things to your browser, good job DNS expert guy facepalm.
00:26:48
SolarWinds wasn’t a Russian mole Gregory, it was code submitted well in advance that facilitated backdoor access, Google exists for a reason, anyone can check into anything, please check.
00:27:30
Oh god, SolarWinds was not a DNS issue!!!
Also Command Control.. this is like the 5th time Andy has said it in this interview, not everything is command/control or C2 if you like and God Damn if I’d put that on the Drinking Bingo actual cyber security professionals would be dead from either Alcohol Poisoning or Drowning in Alcohol by now…
00:28:28
Mentions Sunburst which was indeed the Malware backdoor - SUNBURST backdoor malware: What it is, how it works, and how to prevent it - Malware spotlight - Infosec (infosecinstitute.com)
00:29:35
Andy infers that attackers can BCC themselves into communications because of ‘exposed DNS servers’
Firstly No.
Secondly, NO!
What the hell dude?
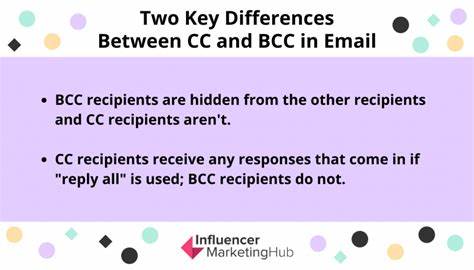
For those unaware in email you can CC (Carbon Copy an email to another recipient, say a work colleague) and you can BCC (Blind Carbon Copy) someone in on the email:
You would need access to the mail server Andy, not the DNS server.
00:30:25
Trying to infer that you could change the content of an email from ‘send troops east’ to ‘send troops west’.
Yeh, nah as above, not DNS again.
00:31:17
Ah the FBI email hack, Pompompurin - 2021 FBI email hack - Wikipedia
That was an interesting time, happy to see that it all boiled down to DNS tampering, obviously.
Defiantly not….. emails sent to addresses taken from the American Registry for Internet Numbers database and the hacker used the FBI’s public-facing email (not the server) system which made the emails appear legitimate. facepalm
00:31:56
CISA 19-01: Mitigate DNS Infrastructure Tampering every single time this gets brought up Andy gets louder… forgetting that that also states how its exploited and it starts with user enumeration to find someone that can make changes to the DNS records not just straight into DNS faffing … facepalm
Also DRINK!
00:32:52
Mo Screenshots, Mo Lies and Red Lines.
00:37:35
Oh-fence. not Offence, Oh-Fence with a big ‘O’
00:37:54
Andy states, quite excitedly, “It’s where remote access came from from the NSA developed remote access okay so they can take over” . It was made by Meridian Technologies. Carbon Copy Plus ring any bells for 1984 folks? pretty sure they aren’t NSA but hey I’m not American and neither is Andy.
00:38:25
Starting to sound like tinfoil hat conspiracy mumbo jumbo.
00:39:12
No University teaches DNS or Assets because they were told not to… by who? where’s your evidence and screenshots for that Andy as that’s sounding a lot like a conspiracy theory again!
00:40:37
Stays all governments are essentially outsourcing DNS to Microsoft. facepalm
Also Evidence?
00:41:00
22.6 Million insecure Microsoft DNS servers again. Again with this number…. The best that we can come up with is he’s found Shodan and started searching random things like ‘dns’ and puts numbers together.
00:41:46
It takes less than six minutes for a cyber gang to infiltrate them
Going to have to ask you to show your math on this one Andy, if you can evidence that it takes less than 6 minutes, I’ll eat a delicious sandwich live on YouTube.
I’m not asking you to do this on live systems as I know you actually would because you strike everyone as “shoots first, misses the target and asks about DNS later”….
Go spin up some test infrastructure (Virtual box or VMware if you like as then people can also test and verify) and prove it once and for all.
Show the entire world what a missing SSL cert on a site can do to DNS.
~Crickets~
00:41:55
Oh god he’s talking about swinging appendages again, why won’t he stop talking about that… He’s obsessed!
00:42:15
Unredacted Screenshot:
Andy’s trick of using a hyphen and then mail protection etc etc etc, same old trick from same old conman…
00:47:30
4th Book plug is not subtle.
00:43:46
80% of all Cyber Attacks in the world are against America.
Proof?
00:44:50
‘Keyboard Warriors’ doesn’t mean what you think it means.
00:46:31
This isn’t like the old days of VHS and BX videos there is only one version you can only do it one way and that’s through websites servers and domain name systems
Actually there is, in the military terms SIGING and HUMINT, Signals Intelligence (websites servers and domain name systems) and Human Intelligence (Spies, James Bond and cool gadgets, oh and local knowledge, insider threats etc)
I think you are going about this the wrong way dude.
00:46:26
No, CDNs or Content Distribution Networks are not friggin’ DHL or FedEx for packets.
They are ‘nearby’ Storage for data.
Let’s take Azure for example, I put a picture that I want showing on my website Into an Azure Storage Container and then take a link provided by Azure and paste in into my site or embed it into my site.
Now when people in America look at my site the image will load faster from a nearby Azure data server, when my readers in Japan load up my site, same thing a Data Centre nearby to them will load the image.
It’s not exactly Rocket Salad but it’s a fairly straightforward way to explain what a CDN is.
00:46:56
Talking about accessing the DarkWeb… oh god don’t follow a damn thing these people ever say about accessing it, ever!
00:48:04
DDoS attacks using DNS to flood sites to fall over and go offline.
Just read this, it’s pretty cut and clear on what exactly does what and guess what, DNS isn’t mentioned once on the page (go on Ctrl+F to find ‘DNS’ on the page) - Understanding Denial-of-Service Attacks - CISA
00:49:24
Rogers ‘outage’ in 2022 was a BGP error - Cloudflare’s view of the Rogers Communications outage in Canada
Similar to what happened to Facebook when it disappeared off the internet for a bit, that was hilarious!
The ‘hack’ though was an issue with Log4J by Pom.
00:52:16
this isn’t just about your ego or your appendage swinging or the four letters after your name
OH GOD WHYYYYYYYY????!?!??!?!!! Stop with the Swinging Appendages dude people are going to start drawing lines and making conclusions.
People actually semi take me seriously because in a serious conversation I won’t say stupid things like this, it’s called ‘professionalism’, go look it up.
00:52:39
The high net worth login for Bank of America was not secure it was actually displaying and not secure
So you mean a login page didn’t have an SSL cert? is that what you actually mean?
Also was this you trying to log in with your, unfortunately corrupted browser? Meaning it likely wouldn’t have tried to divert to HTTPS or was it the customer trying to log in because at this point I feel like the customer logging in would have shown an SSL Secured marking.
00:53:43
Andy sends me these things obviously heavily redacted just to give me an idea of what’s happening out there in the real world
No, he sends you them heavily redacted because you would be inclined to actually check and verify before speaking about them and it is very likely you would see through his grifting Gregory.
00:55:14
Mentions the Electoral Commission hack in the UK, Andy tried the screenshots on that one too:
Disproved.
00:59:02
I had the Good Fortune to sit down with the air commander of the UK Academy for the ministry of Defense okay he’s now retired I won’t name him for fear of embarrassment
That’s not embarrassment, he will probably rip you a new one for taking things out of context.
01:00:34
Who checked the DNS servers?
I knew there would be one in there, took a bloody hour, he can’t help himself. He’s implying DNS was the cause for a hack in the Ministry of Defense Academy in 2020.
01:02:03
That F35 that went down, yep DNS server issue, clearly…
01:03:07
If a company that are manufacturing say f-35s or Trident submarines or anything else if their website isn’t secure it means unfortunately in yesteryear of warfare they had to wear a uniform you knew who the enemy was now one there’s very little attribution
Tries to blame Tor for facilitating leaks and tries to imply that an SSL cert on www.heyitstheleakedtridentsubmarineblueprints.com is the reason that the blueprints were leaked.
Even The Onion would have a hard time making up headlines for articles in comparison to Andy and his grifting.
Fin.
Thank f**k.
Christ my entire day has been derailed because of this one hour six minute video interview and you know what’s worse?
Any audience that is uneducated in cybersecurity will lap it up and take it as gospel that Andy is speaking the truth.
This needs to end.
Andy is Weaponizing Information and turning it into Misinformation and Disinformation.
Please read my articles, posts, breakdowns, comments, they expose the lies and cons that Andy is playing.
I honestly thought I could take a break from the Andy post stuff, I thought I could refocus, kick back off my learning and get a role sorted out at a company that I will never publicly name as I don’t want Andy or any of his ‘Cronies’ finding out and hounding them with made up facts and figures…. even thought up a cool ‘pen name’ for any articles I may construct for companies so no one would ever know its me….. I thought maybe he had learned his lesson after exposing lie after lie that he has told but apparently not.
It is now 1:18pm.
I am having a break now for food.
Be safe folks.
Ask Questions.
Fight FUD and Misinformation.
Never back down from a charlatan.
Peace be with you.
Live long and prosper 🤙
I don’t have any sponsors or anything but if you enjoy my work, or feel sympathy for my wife, then I have set up a Ko-Fi account as well as a BuyMeACoffee people can donate to.