FUD Fighters - a mini update
Good morning dear readers, it’s been a while since I wrote out an article, I know. Normally I would ‘Fast and Furious’ these kinds of things but I have ‘big plans’ for F9 and FX respectively as such this is just a mini update.
Why a mini update?
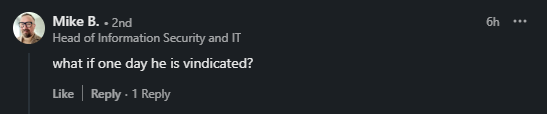
Why indeed, actually the main reason for this is a comment on one of my recent posts, this one actually RE: The Rhode Island cyberattack:
And this comment from Mike B (Sorry I can’t tag you mate but will share this once done):
It got me thinking about the ‘merits of vindication’ and what this would mean for a charlatan who has a history longer than most in this field…. So let’s see what that looks like.
NOTE : This is purely speculative work, any situations or likeness to persons living or dead is purely coincidental. Please keep your arms to your sides at all times in the moving vehicle or you may die and read instructions clearly. Situations described are for entertainment purposes only and viewer digression is advised.
Andy Jenkinson - Vindicated
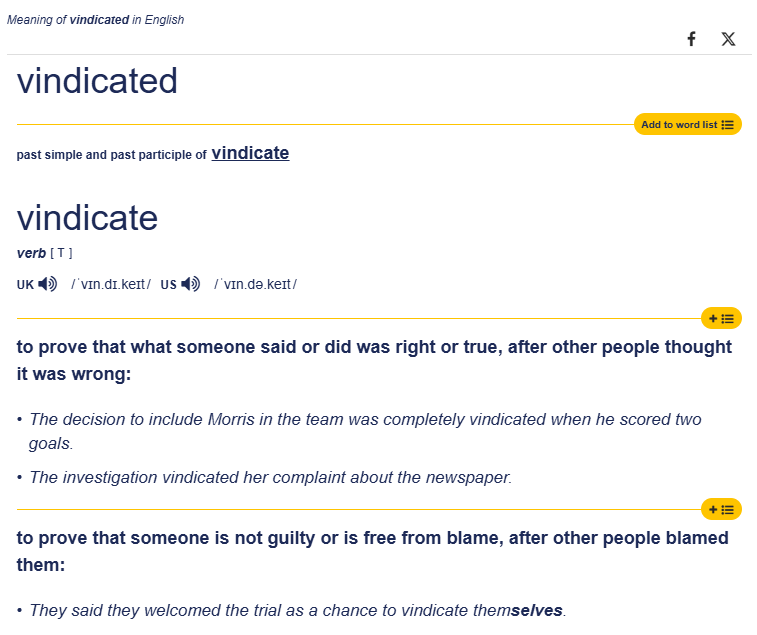
So first we ask ourselves what is the meaning and the purpose of Vindication?
Well the online Cambridge Dictionary - dictionary.cambridge.org states the following:
So the TL;DR is someone proved right after others thought it was wrong OR prove that someone is not guilty/free from blame after others thought it was wrong.
Andy’s Gambit
The issue Andy has with Vindication is that it would mean him facing the actual truth of his boldfaced lies.
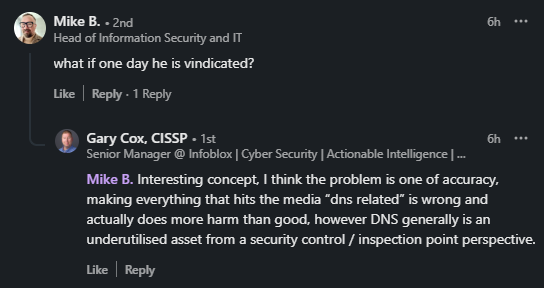
Handily our lord and savior Gary Cox, CISSP touched on this with his response to Mike:
As he notes, Andy’s technique of throwing DNS at ‘everything’ and hoping it sticks, as well as my detailed technical breakdowns of his tradecraft leave very little for people to fill in the gaps of how every screenshot is from DNSviz (or SSLChecker/Tester) and why there are always errors and red line redactions all over the place.
So if Andy were to be Vindicated he would have to open himself up to people criticizing his work as well as him proving his testing methodology.
Act 1 - Being Open
Firstly Andy would need to apologize, not only to himself but to the customers he has contacted, the companies he has hounded and actual cybersecurity professionals he has blocked and smacked down, women in particular, all because he wanted to be the one that was ‘right’ about everything all the time.
That’s a textbook narcissistic trait and one very very difficult to kick.
The reason for that is that a narcissist builds themselves on that deceit and having an infallible nature. To take a brick out of the bottom of the building would mean that the entire structural integrity may come collapsing down and as such they wont do it.
It could take years for him to actually open up about this, this is why we as professionals have been pointing out to Andy that he needs professional help and why I tacked on the end of my posts a while back that he just needs an actual friend to step up and give him the number to AndysManClub or something, just some talking therapy or something.
If Andy wanted to be Vindicated or should I say ‘deemed himself worthy of vindication’ he would need to completely flip his personality and hit this head on.
Act 2 - Detailed Analysis
This is where the ‘True Vindication’ would be, for Andy to be vindicated it means his testing methodology would need to be revealed, no more red lines. It would also mean that he has to show people EXACTLY how DNS got a Cobalt Strike Beacon onto a production server.
Andy’s testing methodology as we have proven time and time again is;
- Go to google/news outlet
- Find new threat
- Go to DNSViz
- Type in ‘target website-com.mail.protection.outlook.com’
- Get screenshot showing errors
- Redact the search query to remove the -com.mail etc.
- Post about it online making up a story that he has been contacting them for years
- Farm likes and comments for vanity
Why do we (as cybersecurity professionals) know this is his methodology?
Well to put it simply, it is trivial to pinpoint what things are when you ask people nicely.
I asked a question and got an answer, I applied that answer to everything I could find when checking and it turns out, Andy is really really predictable.
When you also reach out to the person whom invented DNS and even they say Andy was a nice guy but then he started to go on about certificates and the distaste grew quite quickly as well as said inventor of DNS is also not happy that Andy mentions him and others in ways they don’t prefer and he noted his ‘talent for bypassing the technical people and going to the top of an organization.’
Almost like Andy doesn’t want his methodology looking into for some reason…. 🤔
Andy also cannot to this day answer my simple question of how a beacon made it onto a production server using ONLY DNS as Andy claimed that was the ‘only way it could get on’.
I’ve asked him to spin up Virtual Machines, I’ve asked him to give a video or a talk explaining it all.
Crickets
What did I do during that time? Learned more Python, took a course in Ansible and oh yeah, passed a Penetration Testing Certification Exam… Improvements Vs Stale Sales Technique.
To be truly free and truly vindicated Andy would have to open up this side of his business, the ‘technical’ side so to speak, though not very technical it seems.
Act 3 - User Feedback
With Andy now growing and starting to explain his methodology he would need to be prepared for the torrent of replies from the actual professionals in the field as well as any irate customers wanting to say their piece.
I say torrent as a feel like a lot of people in the field of cybersecurity are aware of Andy and his grift though not many customers (read: victims) would be as switched onto this.
This is manly because Andy uses his big wrinkly brain to target customers that he knows he can ‘influence’ and potentially blackmail (so to speak, again this is made up and hypothetical).
Because they would now be able to flip the script, Andy would need to be open and explain himself to them and bare the brunt of their feedback be it positive or negative.
The feedback from the professional side would likely be the same, as everyone who he has blocked for whatever reasons would now be able to finally say their piece, if any, and leave it at that, adding him to whatever blacklist for email they wish to use.
Andy would need to take the weight of all that pain and all those comments and eat it, and the guilt, vowing to never again try and game the system to his advantage.
No more ‘Pay to win’ presentations to other VCIO, VCSO, CIO, CEO, COO other C-level titles.
No more positive feedback cycle.
Just the truth.
Act 4 - Total Financial Ruin
Since at this point Andy has revealed his secrets it is incredibly likely that companies would want to stay as far away from a conspiracy theorist as possible, so no new business comes in. This also opens the door for companies that have previously had dealings with him, as now they have leverage to question his testing and reporting meaning that as nothing of actual value was resolved, they would likely be a bit cheesed off and seek legal compensation for his actions (some of which have left companies worse off after he left… thank god they went to someone else and actually got square again, allegedly).
As CIP is already in the hole and the hole keeps getting deeper Andy would have no choice but to loose his, I think, 50k stake(?) in CIP and let the company and money fold into oblivion (bankruptcy).
Again though declaring bankruptcy doesn’t really save him as the weight of his debt and years of lies would weigh heavily on him for the rest of his life.
It sounds harsh and that’s because it is, I’ve seen people be completely destroyed by things like this and in all honestly people have (committed seppuku) for a lot less.
Andy’s ‘True Vindication’ is not as easy as it seems.
It is worth pointing out at this moment that again and since the very beginning of my breakdowns of Andy’s posts;
No cybersecurity professional has said DNS is ‘not important’ it just doesn’t work the way Andy thinks it does.
It’s not exactly rocket salad, but this was something Andy and his internet daddy used to infer, by infer I mean this is something Andy has said and his daddy has reposted claiming Andy to be the cyber messiah.
On the subject of Vindication, let’s have a quick look at some of Andy’s recent posts, I’ve highlighted the important things:
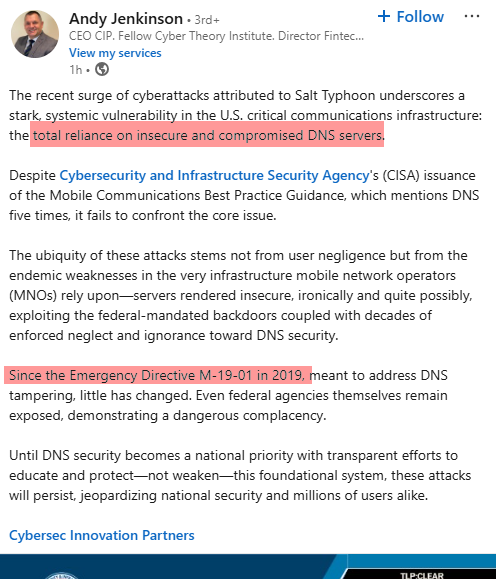
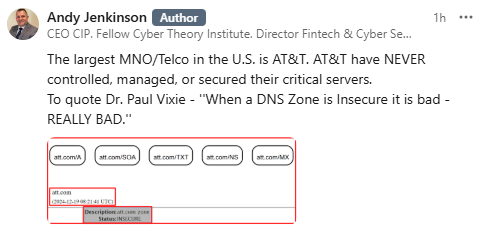
Claims ‘insecure servers’, bet the screenshots are from an bogus MX query on DNSviz:
Yep.
Also M-19-01 Andy’s favorite Directive to clamor onto as we have shown time and time again, additionally that doesn’t explicitly say DNS is the ‘major’ issue, the attacker needs to have access first to someone that can make changes to DNS entries so access before DNS, got it.
Next post:
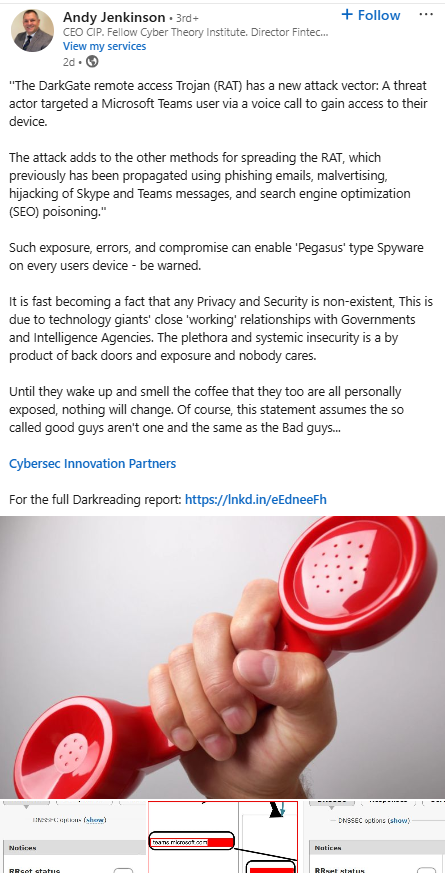
Post about a RAT (Remote Access Trojan).
Pictures are from Microsoft being entered into DNSviz.
Yes that will work…..
🤦
Next:
Another one Andy likes to hang onto, Royal Mail.
Always contacting the CEO directly, always with the DNSviz screenshots showing errors, this is why they are ignored… Additionally Andy has shown that his ‘contacting them directly’ has been DM’s on LinkedIn which a majority of people ignore anyway.
Paper trail lad, paper trail!
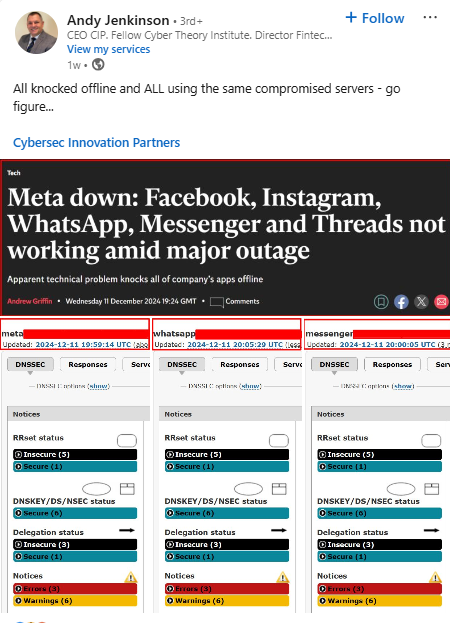
Another one:
Compromised servers < Falsifying Evidence using DNSviz.
Really really predictable.
Please remember this work is a fiction and takes a look at what Andy would need to do to become Vindicated.
His posts however, which clearly show what he is doing and how he is doing it…. That’s all real and live right now.
I may update again before the new year but things are really ramping up IRL and there are about to be some massive changes, and we can only hope for the best for my Mother In Law.
Be safe all, it’s Christmas so nearly time for some global outage again, bet its caused by “DNS”.
Peace
🤙
I don’t have any sponsors or anything but if you enjoy my work, or feel sympathy for my wife, then I have set up a Ko-Fi account as well as a BuyMeACoffee people can donate to.